Wireshark Phishing
 Wireshark Phishing Wireshark Phishing
|
 Tolkien Ring Tolkien Ring
|
 Sparkle Redberry Sparkle Redberry
|
|
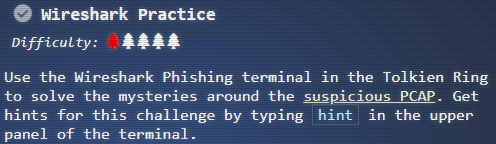
Objective : Use the Wireshark Phishing terminal in the Tolkien Ring to solve the mysteries around the suspicious PCAP. Get hints for this challenge by typing hint in the upper panel of the terminal. |
|
|
|
|
|
PCAP file : |
|
We type "yes" on the terminal and that prompts a series of questions.
|
|
|
|
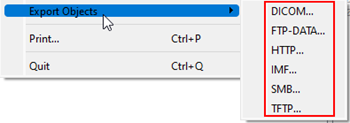
Question 1 : There are objects in the PCAP file that can be exported by Wireshark and/or tshark. What kind of objects can be exported from this PCAP |
|
|
Answer : http |
|
|
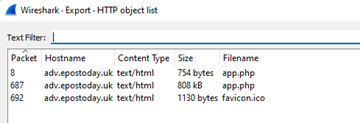
Open the suspicious.pcap in Wireshark and go to File > Export Object. We choose every option there and see exportable items in the list only when we select HTTP |
|
|
|
|
|
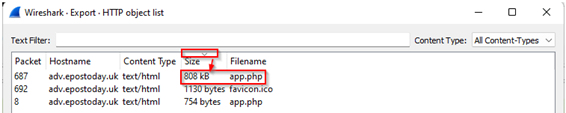
Question 2 : What is the file name of the largest file we can export? |
|
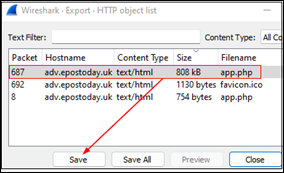
Answer : app.php |
|
Open the exportable objects by clicking on File > Export Objects > HTTP. Sort the objects by clicking the Size column in descending order. app.php is of largest file (808 KB) |
|
|
|
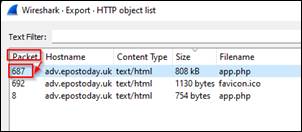
Question 3: What packet number starts that app.php file? |
|
Answer: 687 |
|
In the Wireshark exportable objects under HTTP, app.php shows to start from packet number 687 |
|
|
|
Question 4: What is the IP address of the Apache server? |
|
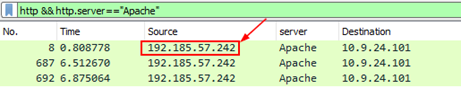
Answer: 192.185.57.242 |
|
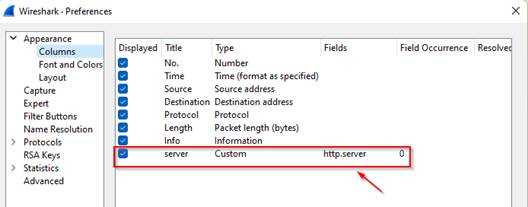
Added a new column named with "http.server" to show the server name and put the below filter http && http.server=="Apache" |
|
|
|
|
|
Question 5: What file is saved to the infected host? |
|
|
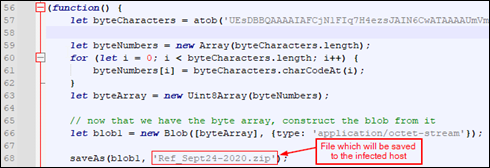
Answer : Ref_Sept24-2020.zip |
|
|
Save the app.php from the exportable HTTP objects. |
|
|
|
|
|
|
|
|
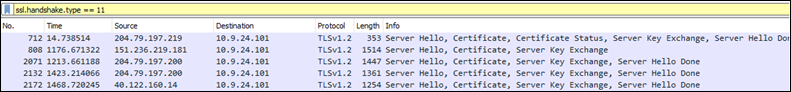
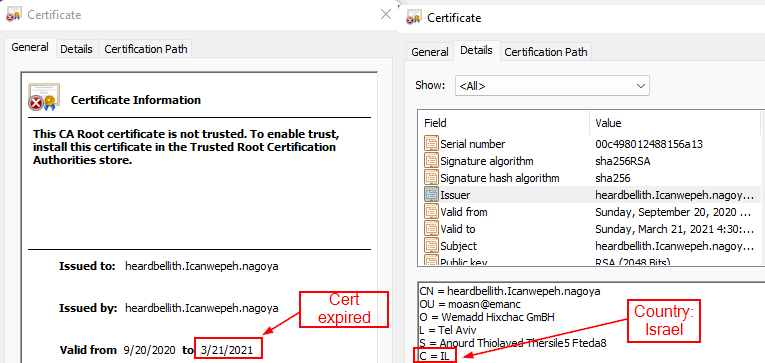
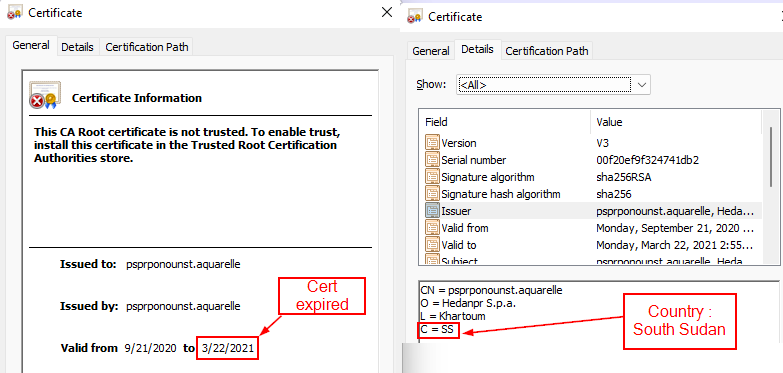
Question 6: Attackers used bad TLS certificates in this traffic. Which countries were they registered to? Submit the names of the countries in alphabetical order separated by a comma (Ex: Norway, South Korea). |
|
Answer : Israel, South Sudan |
|
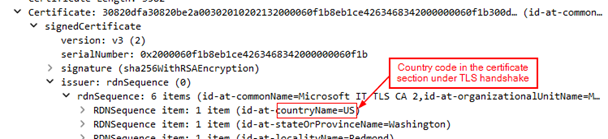
The challenge provides a URL as a hint. This has the filters for TLS traffic in the Wireshark pcap file. Filtering with ssl.handshake.type == 11, below would get us the certificates sent. For the selected packet we can look the certificate section and get the country code of the issuer. Looking at all the available packets, we get the
following country codes : IL,SS where the certificates are not valid |
|
|
|
|
|
|
|
Question 7 : is the host infected (Yes/No)? |
|
Answer : Yes |
|
We know the file Ref_Sept24-2020.zip is being saved via app.php.
So first we take a look at the zip file. |
|
|
We unzip the file and see a file named "Ref_Sept24-2020.scr" in it. |
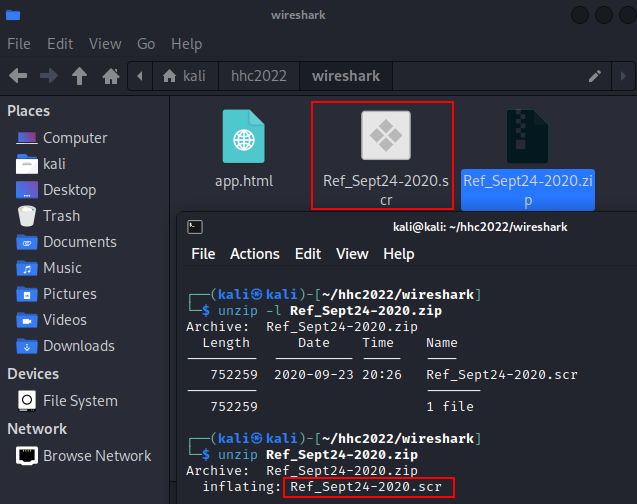
|
|
Calculate the MD5 hash of the file.. |
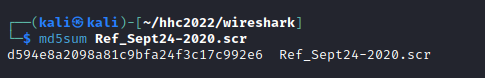
|
|
Submitting that MD5 hash to the Virustotal shows 45 security vendors and 4 sandboxes flagged this file as malicious.
|
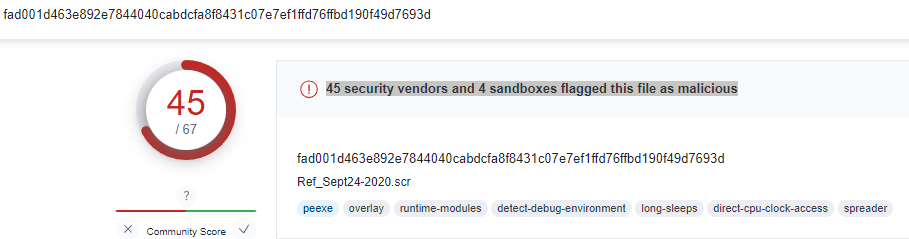
|
|
The objective is now completed, and we
get 5 coins as well. |