Windows Event Logs
|
|
|
|
|
|
|
Windows Event log file (.EVTX) |
|
|
In the terminal, we are asked a series of questions from the .EVTX file. |
|
|
As the 1st step, we convert the powershell.evtx to CSV
|
|
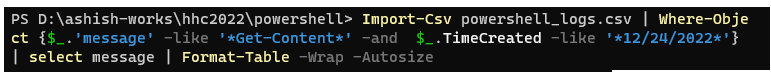
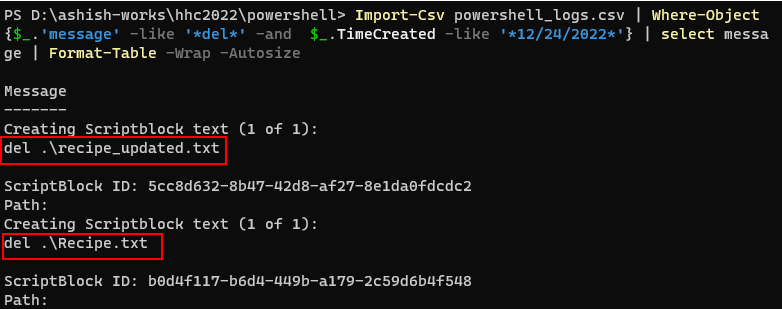
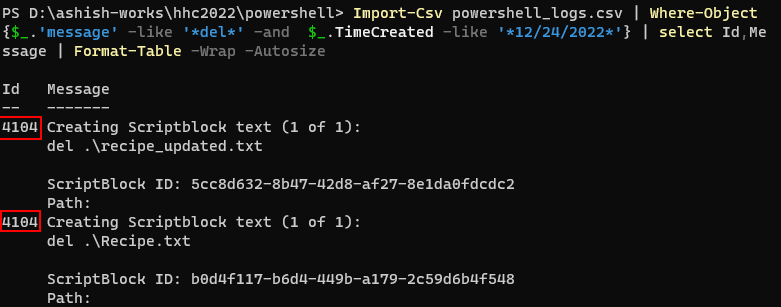
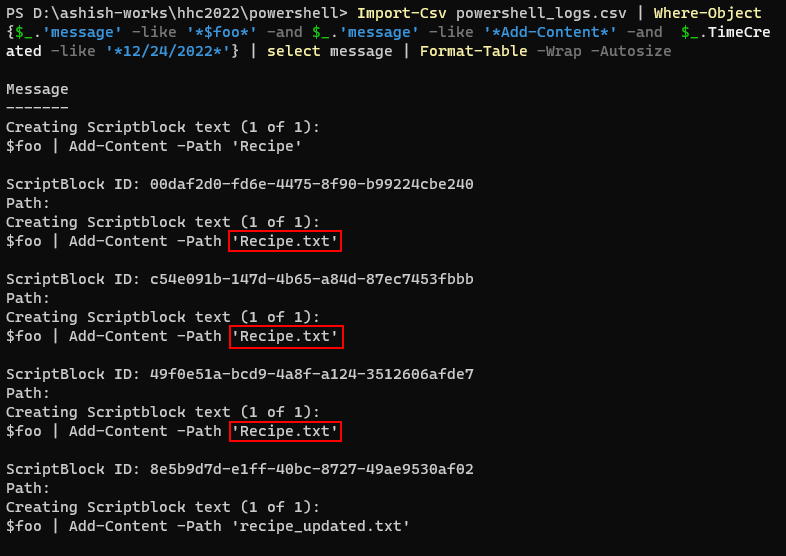
Q5. The attacker ran the previous command against one file multiple times. What is the name of this file? |
|
Answer : Recipe.txt |
|
|
|
|
Q9. Is the secret ingredient compromised (Yes/No)? |
|
Answer: Yes |
|
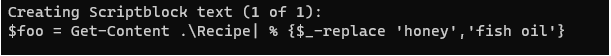
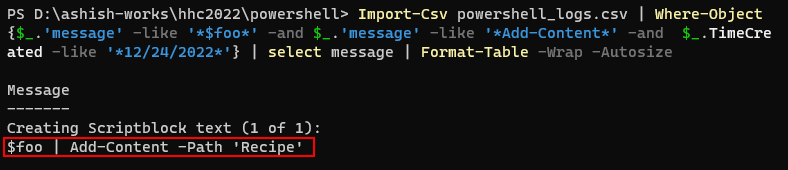
This is because : # The attacker got the content from original recipe file and replaced the honey with fish oil and put that updated value in the variable $foo
And then wrote the changed variable back to the original file named Recipe
|
|
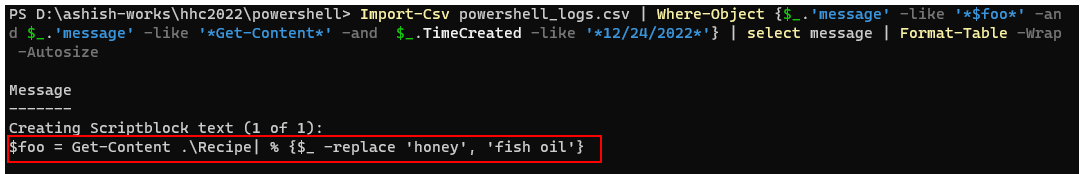
Q10. What is the secret ingredient? |
|
Answer: Honey |
|
From the answer to the question 9) the ingredient which got replaced in the original recipe file was honey. Therefore, the secret ingredient is honey 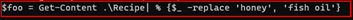
|
|
The objective is now completed and we get
10 coins as well |