Where in the world is Carmel Santaigo
 |
Hints from Tangle Coalbox Turns out some elves have gone on some misdirected journeys around the globe. It seems that someone is messing with their travel plans. We could sure use your open-source intelligence (OSINT) skills to find them. Why dontcha' log into this vintage Cranberry Pi terminal and see if you have what it takes to track them around the globe. If you're having any trouble with it, you might ask Piney Sappington right over there for tips. |
Tangle Coalbox indicates another elf named “Piney Sappington” may have some hints on how to solve this objective.
So, we head over to that elf now who is also present in the courtyard.
 |
Hints from Piney Sappington You see, I've been looking at these documents, and I know someone has tampered with one file. Do you think you could log into this Cranberry Pi and take a look? It has exiftool installed on it, if that helps you at all. I just... Well, I have a feeling that someone at that other conference might have fiddled with things. And, if you help me figure this tampering issue out, I’ll give you some hints about OSINT, especially associated with geographic locations! |
In the terminal we are presented with the below problem:
HELP! That wily jack Frost Modified one of our naughty/nice records, and right before Christmas! Can you help us which one? We’ve installed exiftool for your convenience!
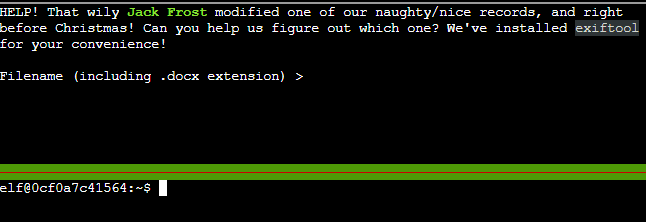
We will get the Last Modified By attribute value for all the docx files and then grep the output it with “Jack”.
That should give us all the files which were last modified by Jack Frost.
We have -C 5 in the grep so we can get the lines around the matches for the context.
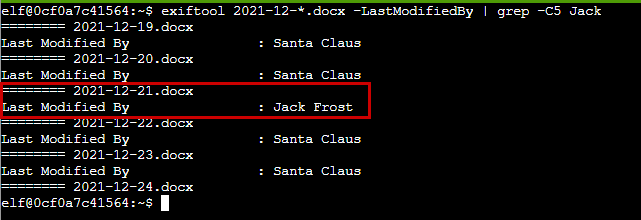
Command entry and output :
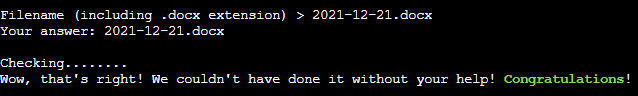
Answer verification :
Achivement Unlocked :
Hint Unlocked :
The “flask cookies” hint is actually a Github Gist from Mr. Chris Elgee.
https://gist.github.com/chriselgee/b9f1861dd9b99a8c1ed30066b25ff80b
That above gist shows how one can decode the value in a cookie generated by Flask applications.
Going back to objective #2 we start the game.
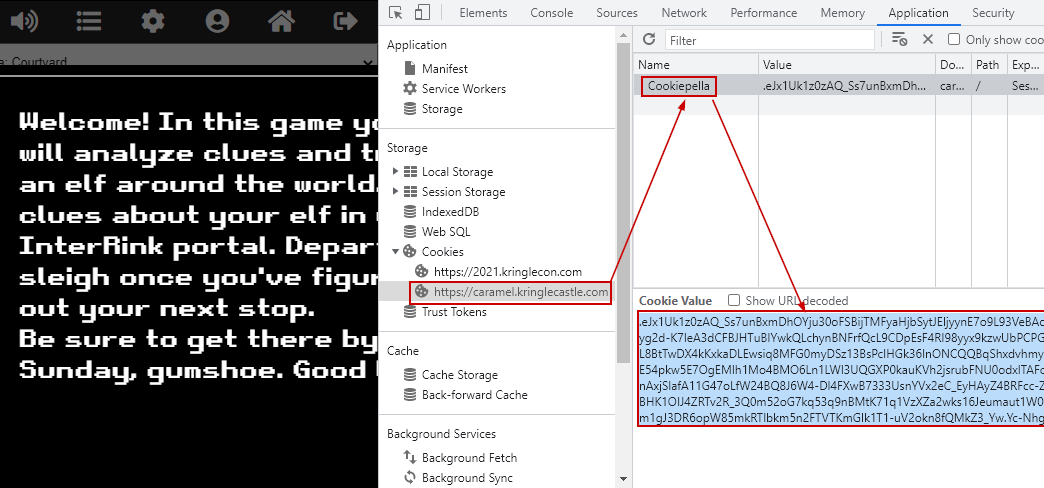
In the browser we open developer tools.
Under developer tools > Application tab there is a cookie named "Cookiepella" for the domain used for the challenge (caramel.kringlecastle.com).
We follow the instructions to decode the value in the flask cookie to JSON.
cookie = "<value of the cookiepella cookie>"
import zlib; import itsdangerous
zlib.decompress(itsdangerous.base64_decode(cookie))
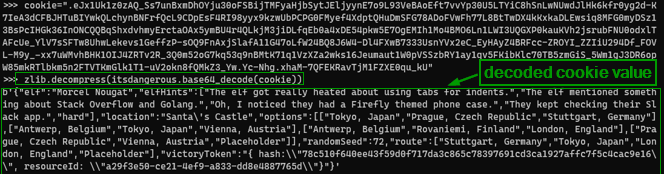
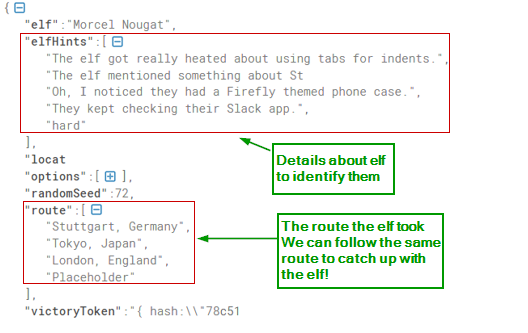
We format the output JSON for better understanding.
The JSON has details about the elf to identify them.
The JSON has also has the route the elf took. We can take the same route to catch the elf.
On the visit interlink page, we supply data we have in the decoded flask cookie and click on "Filter Elves".
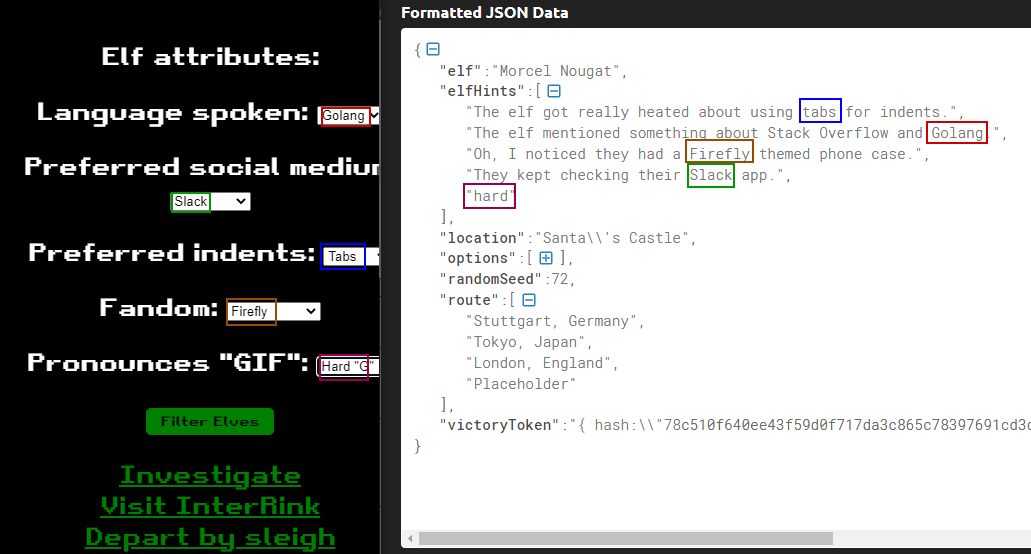
The elves have been filtered out based on the data and possibly Its Morcel Nougat and their location was "Santa's Castel"
Both of these datapoints are also in the decoded cookie value.
Note the route taken by the elf in the decoded cookie value:
Stuttgart, Germany > Tokyo, Japan > London, England > PlaceHolder
We click on "Depart by sleigh" to follow the same route to catch up with the elf in London, England.
| In London, England, we notice there is no option to "Depart by Sleigh" which indicates we are close to the elf. We click on Investigate. |
We are presented with 3 investigate options. |
|
 |
When we click on "Investigate 1", It says we have caught up to the elf.
We are given the option to guess the elf.
We choose "Morcel Nouget" since Its also in the name of the elf in the decoded cookie.
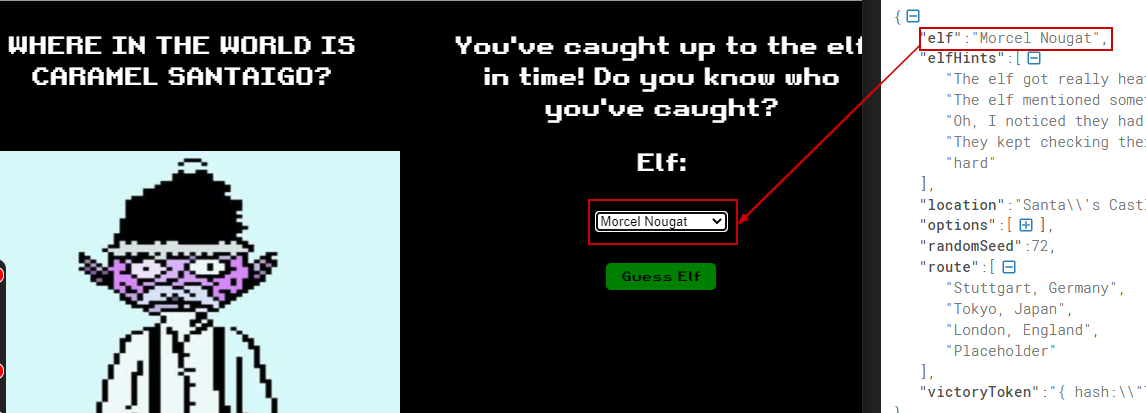
Upon selecting the elf and clicking on the “Guess Elf”
The message "You've won" appears which means we have completed the challenge.
