Strange USB Device
|
Challenge : Assist the elves in reverse engineering the strange USB device. Visit Santa's Talks Floor and hit up Jewel Loggins for advice. |
||
Difficulty Level :  |
Location : Santa’s talk floor |
Elf/Troll :  Morcel Nougat Morcel Nougat |
|
Hints from Morcel Nougat : Do you know anything about USB Rubber Duckies? I've been playing around with them a bit myself. Please see what you can do to help solve the Rubber Ducky Objective! Reference Talk by Kevin Tyers HIDden Duckey, Deconstructed Payload |
We open the terminal and presented with a question
Question: What is the troll username involved with this attack.
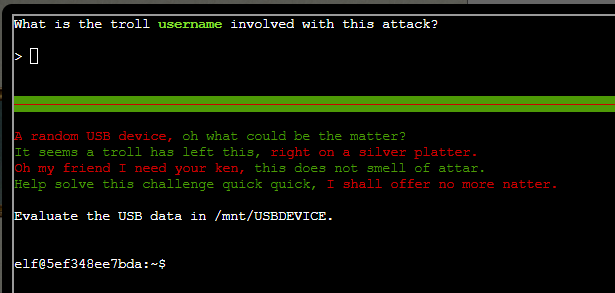
We see there is an inject.bin under /mnt/USBDEVICE
We do the file listing and we see a python file named “mallard.py”.
If we look at the contents of the file, we see the python script takes an "inject.bin" file as an input
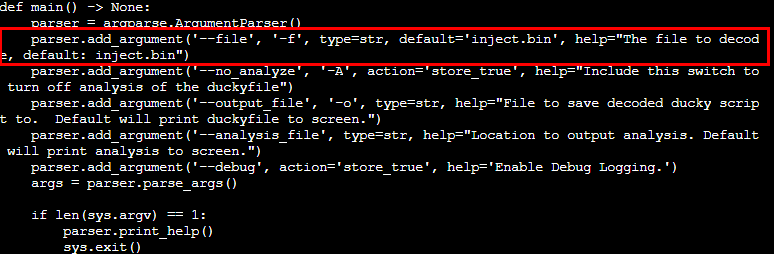
We run the mallard.py with the inject.bin as input.
python ./mallard.py --file /mnt/USBDEVICE/inject.bin
The rubber ducky binary inject.bin is decoded.
We see a few interesting things being done in the original file.
Numbered in the screenshot below :
- There is a hardcoded base 64 string which looks like reversed ("==" in the front)
- The "rev" used to reverse the already reversed base64 string making it a proper base64 string.
- "base64" command with -d switch to decode the base64 string
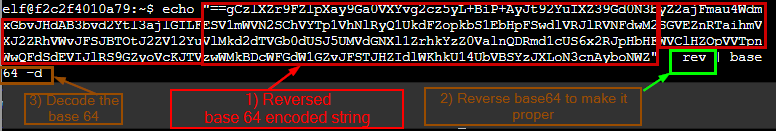
So we take the above line from the source code and execute in the terminal
The base64 is reversed and decoded to reveal the user’s name.
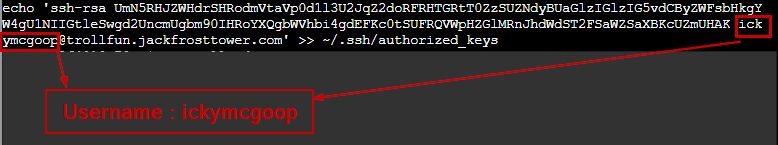
In the above an authorized_key file is getting created with the public cert for the user ickymcgoop.
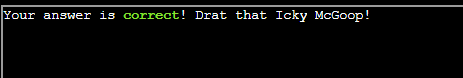
The answer is ickymcgoop
We submit that username as the answer.
The answer gets accepted and we complete this objective.